My talk at Complex Adaptive Systems, Chicago (2011)
I’ve just returned from the Complex Adaptive Systems conference on Wednesday after an eight hour drive — well, most of the driving was done by Dr. Obimbo and Haochen. I presented my paper An evolutionary computation attack on one-round TEA. This paper is built on top of my course project in Computer Security (University of Guelph, Winter 2011). This is my first cryptanalysis paper, and is an aside to the bioinformatics focus of my thesis.
My slides introduce Tiny Encryption Algorithm (TEA) pretty well, along with Genetic Algorithm (GA) and Harmony Search (HS). The slides detailing the results aren’t quite as self-explanatory, but are bearable since the theme is fairly easy to establish: simpler keys are easier to break than more complicated ones.
>>> Download: CAS2011Chicago.pdf — my presentation from Chicago. <<<
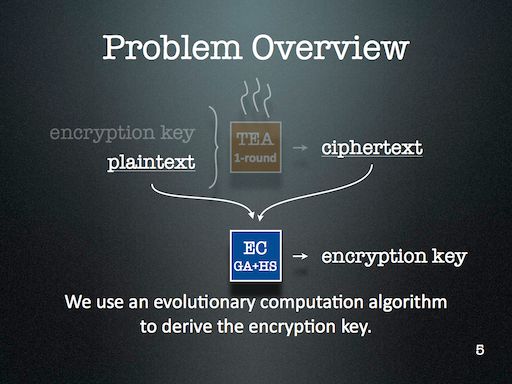
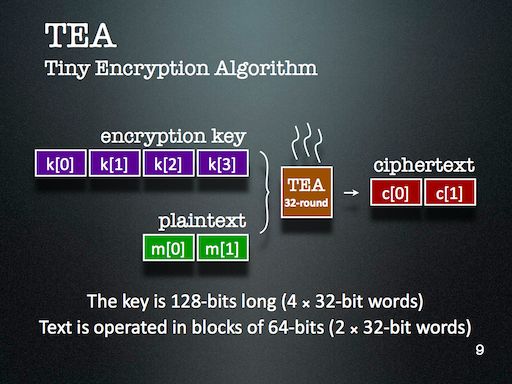
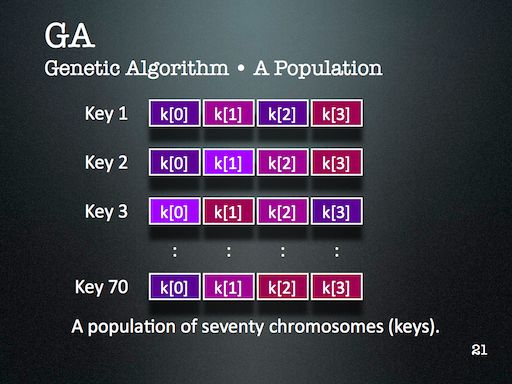
I might look at cryptanalysis again in future — but I’ll certainly use Evolutionary Computation (EC) again. It’s just too readily available in my toolkit, and is far too easy to deploy. One of the major lessons of this project that became very clear through during discussion with the audience is that the operators that are part of an EC algorithm should reflect the kind of problem we’re trying to solve. This might seem obvious at first, but I think it’s more subtle than that. For this project, HS enabled the EC to probe a keyspace with many repetitions — something that GA operators alone didn’t provide us.
In general however, the solution space is lumpy enough that using ECs against stronger encryption schemes is just not viable — unless the EC had some magic to overcome the linearly inseparable lumps. I haven’t yet met such an operator and am not convinced one way or another about its existence. I’ll certainly introduce you if I ever do bump into it 😛
 Ed's Big Plans
Ed's Big Plans